Advanced Authentication Techniques in Zero Trust Network Access
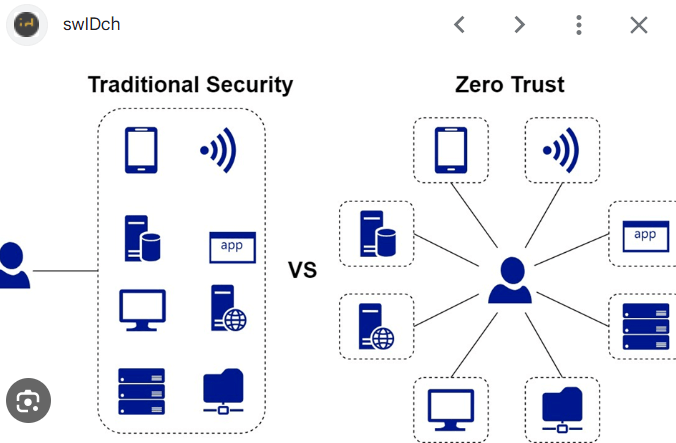
With the growing complexity and frequency of cyberattacks, the need for stringent access security has never been more compelling. The traditional username-password combination can no longer be expected to prevent breaches in an age when users can access resources from anywhere and on any device. New context-aware modelling for authentication, which continuously revalidates trust, is warranted by Zero Trust Network Access (ZTNA). This will ultimately require advanced methods of authentication in order to achieve the risk-based dynamic access control which is needed to counter the limited static credential authentication methods.
The Role of Authentication in Zero Trust
ZTNA is based on the principle of “never trust, always verify.” In a Zero Trust conditional access configuration, any access attempt made by a user, device, or application is considered untrusted until fully authenticated and authorized. Authentication in Zero Trust should never be regarded as a single event; rather, it is a continuous process that is carried on for the duration of the user’s session.
Along these lines, ZTNA operates with advanced authentication methods that go far beyond traditional login solutions to instil confidence in identity and reduce needless friction for legitimate users, evolving with a fast-evolving threat landscape.
Key Advanced Authentication Techniques in ZTNA
Multi-Factor Authentication (MFA)
MFA is, in fact, the baseline requirement in every Zero Trust model: it states that the identity of a user must be validated by submitting two or more independent credentials, such as:
- Something you know (password or PIN)
- Something you have (security token, mobile device)
- Something you are (biometric data)
MFA is used for the attestation of the user not just at the time of direct access, but also continuingly throughout a session.
Adaptive (Risk-Based) Authentication
Adaptive authentication is about measuring risk relative to a certain access request based on factors such as:
- Health and security posture of the device.
- User behaviour and access history.
- Location and time of access.
- Network characterisation, such as access through VPN, TOR, and IP reputation.
Depending on how risky a login attempt appears, access may trigger escalation in authentication requirements like MFA or blocking entry completely. Certain low-risk users may, however, enjoy a more smoothing experience.
Biometric Authentication
Biometrics is a crucial building block of ZTNA platforms. Those biometric modalities that are gaining popularity in ZTNA platforms would include:
- Fingerprint scanning
- Facial recognition
- Voice recognition
Biometrics provide high-assurance identity verification, and they are a lot more useful for entirely mobile-first workforces or people operating in very high-security environments. Beyond that, it removes all theft risk from stolen credentials.
Device Certificate Authentication
In ZTNA, not just the user is authenticated, but also the device. Device certificates are unique identifiers and authenticators for trusted devices, ensuring that only managed and compliant hardware can connect to the network. This is primarily useful in a bring-your-own-device (BYOD) scenario.
Password-free Authentication
Brought forth by ZTNA, these features would cause seismic shifts to change sign security from a password model to using:
- Biometrics
- Magic links
- Hardware tokens – like a YubiKey
- One-time codes via email or app-based authenticators
Passwordless approaches will lower the windows of possibility for phishing, brute force, and credential stuffing, while providing a great customer experience.
Continuous Authentication
ZTA supports the continuous verification of identity throughout the session using behavior patterns that adapt to the demands of authentication. Behaviour patterns monitored during an ongoing session include keystroke dynamics, mouse movement, and session length; should suspicious behaviour be detected, access may be revalidated, restricted, or terminated in real time.
Federated Identity and Single Sign-On (SSO)
ZTNA works with identity providers (IdPs) that have federation identity support based on standards such as SAML, OAuth, and OpenID Connect. Because of this, secure and seamless access is possible over multiple platforms, using a single set of verified credentials subjected to advanced authentication mechanisms.
Conclusion
Intelligent access decisions are undeniably intelligent, contextual, and sustained against modern threats that take a serious toe to the core of the Zero Trust model. A ZTNA builds a strong layer of identity assurance in today’s hybrid, cloud-first world by supplementing biometric, adaptive, and continuous authentication technologies with password-based models; it is a fitting complement to replication. Adoption of these technologies will harden defences, making for easier and more frictionless the hallmark of security without compromise.




